Basics
- Project TitleRisk Management in Cyber-security: Running a Vulnerability Scan
- Employer SiteLeominster Credit Union
- Submitted By (Teacher Name)Richard Duncan
- SchoolMontachusett Regional Vocational Technical School
- Brief Description and RationaleCourse: Cybersecurity Operations
Unit: Vulnerability Scanning
Goal:
To have students conduct vulnerability scans on Windows and Linux systems to identify and eliminate weaknesses.
Rationale:
A cybersecurity analyst must know how to secure host computers from malware and outside attacks in order to protect company data. As an analyst, you may be tasked with some or all of these responsibilities. A company‘s data is its most valuable resource and it must be protected.
Essential Question:
What are the typical vulnerabilities that must be identified and eliminated according to best practices in the industry? - Grade Level9-12
- Materials / ResourcesIndustry data:
BLS - Bureau of Labor Statistics website (Occupational Outlook Handbook): https://www.bls.gov/ooh/computer-and-information-technology/information-security-analysts.htm
Curriculum:
Cisco CyberOps curriculum: www.netacad.com
Cyberpatriot Competition: www.uscyberpatriot.org
Software:
Hypervisor - virtual image management software: Hyper-V VirtualBox, or VMware
Virtual Images - Windows Server, Windows client, Linux client
CIS-CAT evaluation tool
Hardware:
Windows or Mac PCs -
Web Link: Occupational Outlook Handbook: Information Security Analyst
- Duration of lesson180 minutes (Four 45 minute class periods) total
Install virtual images - 2 class periods (90 minutes)
Configure virtual images - 1 class period (45 minutes)
Install CIS-CAT tool and run vulnerability scan - 1 class period (45 minutes) - Key Vocabulary/Word WallList and define key words that may be new to students or essential to the lesson.
risk management, risk assessment, audit, Information Security Analyst, Cyber Security Analyst, vulnerability, mitigation, malware - Pre-Requisite KnowledgeBasic computer user knowledge on Windows, Macintosh, and Linux systems
Installing an Operating System
Installing software applications - Any modifications or extensions for particular student populations?IEP/504 plans - Extended time, use of computer, digital copies of notes
SEI (Sheltered English Inclusion) modifications - use of translation apps or websites. - Instructional ObjectivesSWBAT:
1. Configure one or more computer systems to run the CIS-CAT vulnerability scanner
2. Run the CIS-CAT vulnerability scanner to reveal any existing vulnerabilities on those systems
3. Update and/or reconfigure those systems to reduce or eliminate any existing vulnerabilities
Lesson Outline | Creation of virtual images
Basic configuration of a network client
- Anticipatory set or lesson opening (to activate students` prior learning or draw student interest or involvement)Creation of virtual images
Basic configuration of a network client -
Web Link: Ubuntu_14.04_on_Windows_7.png on Screenshots – Attachment – Oracle VM VirtualBox
Web Link: Windows_8.1_on_OSX.png on Screenshots – Attachment – Oracle VM VirtualBox
Web Link: End-user_documentation – Oracle VM VirtualBox
- Direct InstructionThe teacher will:
Provide instructions on installing the CIS-CAT software.
Use the SmartBoard to model the proper procedure for the students. - Guided PracticeThe teacher will:
Walk around and monitor the students as they individually install the software on their virtual networks. - Independent Practice/Differentiated ActivitiesThe students will:
Install and configure their virtual hosts at their own pace.
Troubleshoot their virtual network to confirm proper configuration.
Install the CIS-CAT scanner software to run vulnerability scans. -
- Lesson ClosureThis lesson helped students run a vulnerability scan on Windows and Linux computers, which they will most likely be exposed to in an IT job. They become aware of the many types of vulnerabilities that must be fixed.
Proficiency in cybersecurity is becoming an entry level skill that will make the students more valuable in an IT support position. - Summative/end of lesson assessmentStudents will submit their vulnerability reports and their remediation plans through Google Classroom.
Students will be graded on their results from an Exhibition/Practice Round of the Cyberpatriot Cybersecurity competition. -
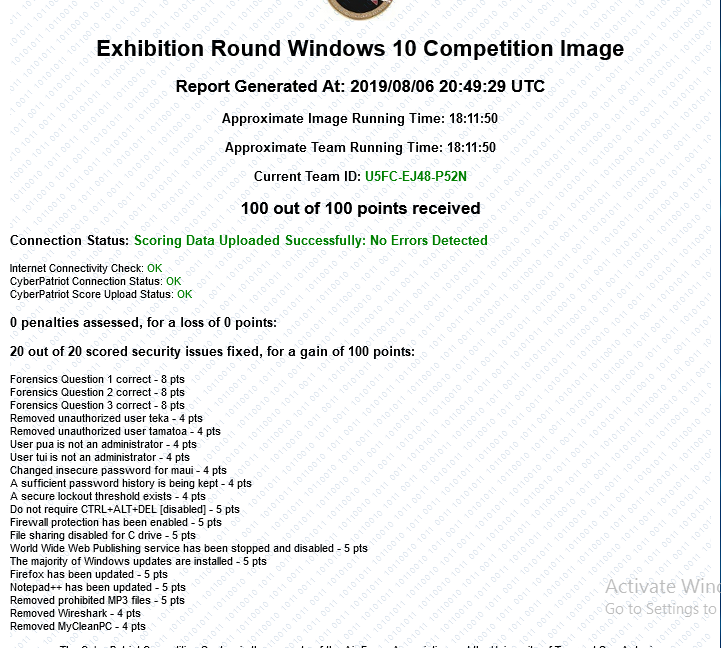

View/Download File: Example Vulnerability Scan
- References / Resources / Teacher PreparationCurriculum:
netacad.com - Cybersecurity Operations (requires instructor certification)
uscyberpatriot.org - free training content
(Other curriculum is available)
Software tools:
CIS-CSAT website
Teacher will have to register to download the free vulnerability assessment tools.
Cyberpatriot website
Teacher will have to register as a Cyberpatriot coach in order to gain access to the Exhibition/Practice Round images (registration is free for practice purposes but if they wish to compete in the actual competition, there will be a fee).
Employment info:
BLS - Bureau of Labor Statistics (research Cyber Security Analyst)
Industry Surveys - GlassDoor, etc. -
Web Link: Occupational Outlook Handbook: Information Security Analyst
Web Link: Cisco Networking Academy Builds IT Skills & Education For Future Careers
Web Link: CIS Configuration Assessment Tool CIS-CAT
Web Link: Cyberpatriot - Archived Training Modules
View/Download File: CIS-CAT Users Guide
Recommended Strategies / Instructional Techniques
- Reading StrategiesOnline curriculum - Cisco Cyber Operations Curriculum
-
Web Link: Cisco Networking Academy Builds IT Skills & Education For Future Careers
Web Link: Cyberpatriot Archived Training Modules
- Multimedia/Visual Strategy (f.e. slides)Powerpoint slides of the curriculum
Chapter 10 of Cisco Cyber Operations Curriculum (copyrighted material) - Graphic organizers or handoutsSupporting content provided in online curriculum and/or posted to Google Classroom.
- Writing StrategiesN/A
- Speaking and Listening StrategiesTeacher Lectures
Student Presentations of Vulnerability Scan - Family: Any opportunities to involve parent/guardians and other family members in this project?Students can run the vulnerability scan on their family computer(s) to educate family members.
Detailed Outline
Tags = cybersecurity | Subject = CVTE | Grade Level = HS | Time Period = School Year | Program/Funding = | Externships-2019 |
Direct website link to this project: http://ContextualLearningPortal.org/contextual.asp?projectnumber=677.2044



